
What is ARP?
ARP is Address Resolution Protocol. It is the fundamental building block of networks today. Basically, it allows devices to learn MAC addresses of other devices on an ethernet network. ARP is widely used to provide a mapping between the data link layer and the network layer of the OSI Model.
What is ARP Poisoning?
ARP Poisoning is a popular man in the middle attack. This attack is carried out over the Local Area Network (LAN). It is used to intercept communication across the network. It allows you to sniff all the traffic between the targets and the internet. If sensitive information like credit card details or passwords is sent unencrypted, it can be easily sniffed.
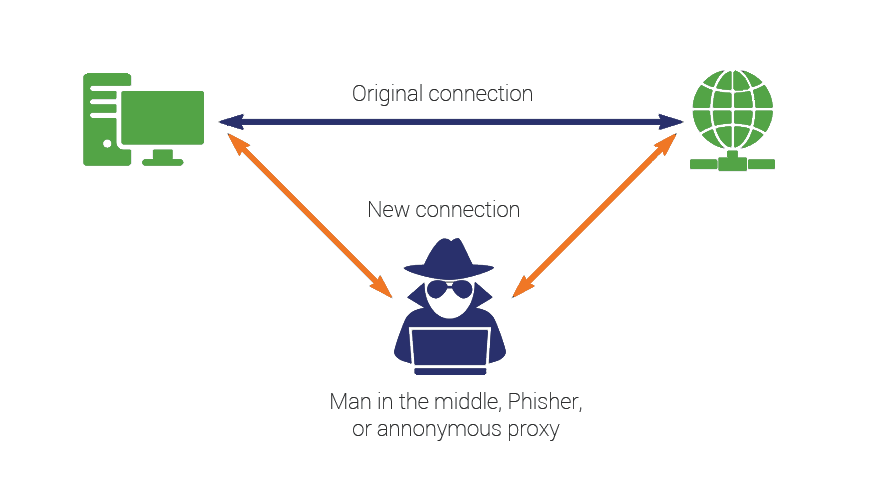
Once the ARP caches are poisoned, an attacker performs a Man in The Middle attack. When the attacker becomes a man in the middle, they can view sensitive information or data flowing between multiple devices and the internet.
How ARP Poisoning works?
There are various tools available over the internet to perform ARP poisoning attacks manually. Also various tools available to automate this attack. An attacker gets into the wireless network within a LAN. Then he poisons the ARP caches in the network between various devices. After poisoning ARP caches, he becomes a man in the middle.
Whenever a victim tries to access the internet, all the traffic can be monitored by the attacker. All the URLs, HTTP requests, etc can be monitored by the attacker. He can also manipulate the victim to give his/her sensitive information. An attacker also can change the DNS servers, configured on his own, to the victim computers.
There is a popular tool available over the internet called Wireshark. Wireshark tool is used by network admins for monitoring the traffic over the network. But an attacker or a hacker can use this tool after poisoning the ARP for monitoring the traffic that flows through their victims and the internet.
How to perform ARP Poisoning?
Note : This tutorial is for educational purposes only.
For performing an ARP Poisoning attack, we will be requiring any Linux Distribution installed on your computer and internet connection. Any Debian Linux/GNU is preferred over any other Linux distribution. Kali Linux is the best hacking OS developed by Offensive Security.
Every computer that connects to the internet has an ARP table. This table just links IP addresses with their corresponding MAC addresses. So if you want to communicate with a certain IP address, the computer will know which MAC address to send it to.
In Linux, you can see your ARP table by typing ‘arp’ in your terminal. If you are using Windows, open your command prompt and type ‘arp -a’ to see your ARP table. Note that the only devices which you have already communicated within the network will show up.
Boot up your Linux distribution(Kali Linux preferred) and open the terminal. Type the following commands in your terminal.
Suppose the gateway IP address of your network is 192.168.1.1 and the victim computer is 192.168.1.9.
This command will forward the packets from your linux operating system.

AS soon as you enter the command , you will become man in the middle.

you can monitor the packet flow by using tools like wireshark or packet capture. And note that if you check the arp table before an after the attack, the mAC address of gateway is changed.
How to defend from ARP Poisoning?
Firstly you shouldn’t be using any clear text protocols like HTTP, Telnet, etc. If in case you are using such protocols it will be very easy for an attacker to capture your sensitive information through the unencrypted traffic. In such protocols, an attacker has clear visibility of all the data that flows between your computer and the internet.
We can stop ARP spoofing or ARP Poisoning by implementing Dynamic ARP Inspection in your network. Dynamic ARP Inspection can be implemented either by DHCP Snooping or manually configure MAC addresses.
In DHCP Snooping, the switch is listening DHCP requests from all the devices to the DHCP Server. And then creating a mapping interface between MAC addresses and IP addresses dynamically. Then if you change your MAC address, the traffic is denied.
Whenever we perform this ARP poisoning attack, the MAC address of the gateway device is changed. If we install DHCP snooping, the device is certainly blocked by the router in the network. This method is implemented by large enterprise companies to stop the man in the middle attacks. And certainly, you can do this in your home network by manually allocating MAC addresses to devices in your network.