
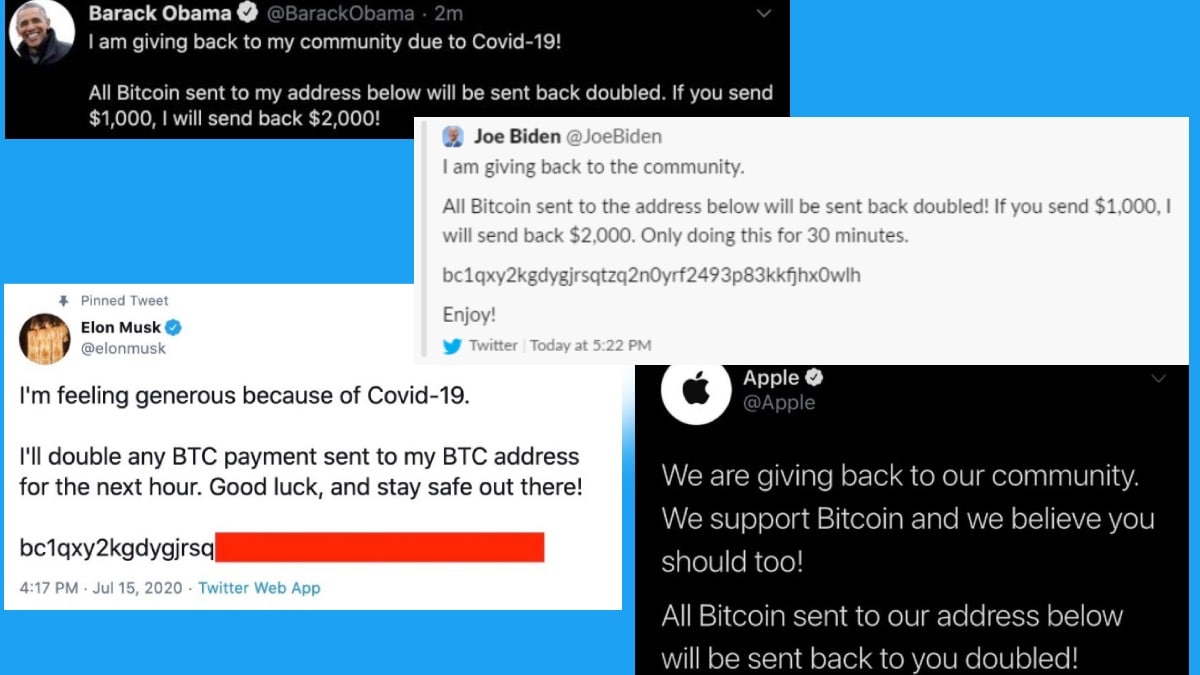
Last year, high profile Twitter accounts like Bill Gates, Elon Musk, President Obama, Joe Biden, Kanye West got hacked. All taken over twitting about a cryptocurrency scam. In this Twitter hack, the attackers got access to internal Twitter admin tools. These tools gave them access to high profile Twitter accounts. They were able to bypass all the security measures such as strong passwords, two-factor authentication, etc.
The scariest part about this attack becomes they did not use traditional attacking methods. Instead, they used social engineering to bypass the system. Instead of hacking into the network or finding bugs to exploit, this attack was governed by hacking minds. Every company’s biggest security risk is its people. Hacking into an employee’s mind is way easier than hacking into a network or system.
How was Twitter hacked?
The news publishers published two stories. One from New York Times(NYT) and one from VICE. Both of these involved two sources. Amazingly, these sources were the people who performed this attack. Twitter officially released a blog that had complete information about this attack. A small number of Twitter employees were manipulated by the attackers. The attackers used the employee’s credentials to gain access to Twitter’s internal system. They targeted 130 Twitter accounts and gained complete access to 45 high profile accounts.
This is the only information that Twitter officially released. But, the VICE and the NYT apparently talked to the attackers behind this. This discussion essentially referenced that the employees got corrupted. The employee was bragging on a discord server that he can get access to various Twitter accounts. The two attackers saw this employee bragging. The employee apparently posted the screenshots of his admin panel. This proved that he actually can access several accounts. But they learned soon after that he wasn’t actually a Twitter employee. This guy used a Twitter employee to gain access to this admin panel.
After investigation, it got proved that this guy gained access to the internal Twitter Slack channel. He was able to see credentials. The VICE interview proved that there was an internal rep. This rep did all the work for the attackers. The second source said that they actually paid a Twitter insider.
The attackers were NOT real hackers
The actual attackers who performed this attack were not real hackers. They had what many hackers dreamed about. But they chose to perform a bitcoin scam. The actual attackers didn’t know how viable this information was. They did not know how to sell these accounts in the hacking community. If they would have planned better for this, they would have known better ways to make more money. For example, they would have found some context to sell this access. From examining all this information, this wasn’t a very sophisticated attack. It wasn’t even like some extremely skilled hackers trying to gain access by finding vulnerabilities. This attack was a pure social engineering attack. Even this attack wasn’t a well-planned attack.
Stages of a Social Engineering Attack
According to EC Council, the four stages of social engineering attack are listed below:
1] Research
2] Select a victim
3] Develop a relationship
4] Exploit the relationship
How to protect yourselves?
One of the best things that you can do now is employee training. Teach your employees about social engineering attacks. Other things include privilege isolation. This means implementing the least privilege in every possible area you can. As it always comes down to an individual person in making sure they protect themselves as well as the enterprise. Most of the time it’s the user or the person that is vulnerable. We have various less occasional things like Wannacry. In Wannacry, the software uses network vulnerabilities to hop inside the system. But in most cases, the malware is injected through some kind of human interaction. For example, whether they clicked the link in a malicious email. Other examples include downloaded a malicious file, a questionable application, or a game from a torrent, etc. Therefore, employee training and privilege isolation are the most effective security against social engineering attacks.
